The original Paper Highlights are followed :->
Original term tossed up was , A peer to peer Electronic Cash System by Satoshi Nakamoto ,the original abstract from his paper was :
Abstract. A purely peer-to-peer version of electronic cash would allow online payments to be sent directly from one party to another without going through a financial institution. Digital signatures provide part of the solution, but the main benefits are lost if a trusted third party is still required to prevent double-spending.
1.Intro
Transactions that are computationally impractical to reverse would protect sellers from fraud, and routine escrow mechanisms could easily be implemented to protect buyers. In this paper, we propose a solution to the double-spending problem using a peer-to-peer distributed timestamp server to generate computational proof of the chronological order of transactions. The system is secure as long as honest nodes collectively control more CPU power than any cooperating group of attacker nodes.
2.Transaction
We define an electronic coin as a chain of digital signature , now the value of electronic coin remains constant through out globe , unlike our local currency like dollars,euros or rupees
A way for insuring the authenticating all transactions without using external sources like bank , would be making the transaction details abstract and using nodes ,nodes are like various center’s at various locations which verify each transaction , and add it to the transaction chain.
3.Timestamp Server
A timestamp is generated by taking a hash of a block of items to be timestamped , Each timestamp includes the previous timestamp in its hash, forming a chain, with each additional timestamp reinforcing the ones before it.
from datetime import datetime
dateTimeObj = datetime.now()
print(dateTimeObj)4. Proof-of-Work
The proof-of-work involves scanning for a value that when hashed, such as with SHA-256, the hash begins with a number of zero bits. The average work required is exponential in the number of zero bits required and can be verified by executing a single hash.
Which in simple terms mean , we need to first verify if that block belongs to correct block chain , by using what we call nonce(basically an unique value for each block ). Then it’s used to confirm a transaction and add new blocks to the chain .
Proof-of-work is essentially one-CPU-one-vote. The majority
decision is represented by the longest chain, which has the greatest proof-of-work effort invested in it. If a majority of CPU power is controlled by honest nodes, the honest chain will grow the fastest and outpace any competing chains.

5. Network :
The steps to run the network are as follows:
- New transactions are broadcast to all nodes.
- Each node collects new transactions into a block.
- Each node works on finding a difficult proof-of-work for its block.
- When a node finds a proof-of-work, it broadcasts the block to all nodes.
- Nodes accept the block only if all transactions in it are valid and not already spent.
- Nodes express their acceptance of the block by working on creating the next block in the chain, using the hash of the accepted block as the previous hash.
This part of blockchain , i failed to implement it .
6.Incentive
This is the part where the miners make a profit ,this adds an incentive for nodes to support the network, and provides a way to initially distribute coins into circulation, since there is no central authority to issue them.The steady addition of a constant of amount of new coins is analogous to gold miners expending resources to add gold to circulation.
7.Disk Space
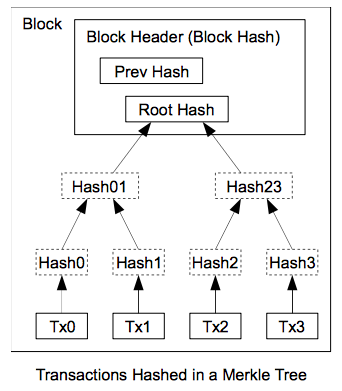
Once the latest transaction in a coin is buried under enough blocks, the spent transactions before it can be discarded to save disk space. To facilitate this without breaking the block’s hash, transactions are hashed in a Merkle Tree [7][2][5], with only the root included in the block’s hash.
8.Simplified Payment Verification
It is possible to verify payments without running a full network node. A user only needs to keep a copy of the block headers of the longest proof-of-work chain, which he can get by querying network nodes until he’s convinced he has the longest chain, and obtain the Merkle branch linking the transaction to the block it’s timestamped in.
9. Combining and Splitting Value
To allow value to be split and combined, transactions contain multiple inputs and outputs. Normally there will be either a single input from a larger previous transaction or multiple inputs combining smaller amounts, and at most two outputs: one for the payment, and one returning the change, if any, back to the sender.
10.Privacy
This part is just know as abstraction of data , of displaying just important information

11.Calculations
The race between the honest chain and an attacker chain can be characterized as a Binomial Random Walk. The success event is the honest chain being extended by one block, increasing its lead by +1, and the failure event is the attacker's chain being extended by one block, reducing the gap by -1. The probability of an attacker catching up from a given deficit is analogous to a Gambler's ruin problem. Suppose a gambler with unlimited credit starts at a deficit and plays potentially an infinite number of trials to try to reach breakeven. We can calculate the probability he ever reaches breakeven, or that an attacker ever catches up with the honest chain, as follows [8]: p = probability an honest node finds the next block q = probability the attacker finds the next block q z = probability the attacker will ever catch up from z blocks behind
include<math.h>
double AttackerSuccessProbability(double q, int z)
{
double p = 1.0 - q;
double lambda = z * (q / p);
double sum = 1.0;
int i, k;
for (k = 0; k <= z; k++)
{
double poisson = exp(-lambda);
for (i = 1; i <= k; i++)
poisson *= lambda / i;
sum -= poisson * (1 - pow(q / p, z - k));
}
return sum;
}12.Conclusion
we proposed a peer-to-peer network using proof-of-work to record a public history of transactions that quickly becomes computationally impractical for an attacker to change if honest nodes control a majority of CPU power. The network is robust in its unstructured simplicity. Nodes work all at once with little coordination. They do not need to be identified, since messages are not routed to any particular place and only need to be delivered on a best effort basis. Nodes canleave and rejoin the network at will, accepting the proof-of-work chain as proof of what happened while they were gone. They vote with their CPU power, expressing their acceptance of valid blocks by working on extending them and rejecting invalid blocks by refusing to work on them.
Blockchain implementation
Basic information ;
It is a way of storing digital data , your choice of storing data is platform independent so :
- Transaction
- Information of crops
- Medical Information
A blockchain is essentially a linked list that contains ordered data, with a few constraints such as:
- Blocks can’t be modified once added; in other words, it is append only.
- There are specific rules for appending data to it.
- Its architecture is distributed.
Enforcing these constraints yields the following benefits:
- Immutability and durability of data
- No single point of control or failure
- A verifiable audit trail of the order in which data was added
Practical Approach :
- Store transactions into blocks :
So we will be using JSON Format ,JSON is a syntax for storing and exchanging data.
JSON is text, written with JavaScript object notation.
How to Convert a Python object into JSON Format:
import json
x = {
"name": "John",
"age": 30,
"married": True,
"divorced": False,
"children": ("Ann","Billy"),
"pets": None,
"cars": [
{"model": "BMW 230", "mpg": 27.5},
{"model": "Ford Edge", "mpg": 24.1}
]
}
convert into JSON:
y = json.dumps(x)
the result is a JSON string:
print(y)
So first Step will be storing data in our blocks in
{
"contributor": "Name of the person contributing",
"Transaction-ID": "Transaction ID ",
"timestamp": "The time at which the content was created"
}
Each block should have an unique ID , for backtracking to the transaction in the block.
2. Add Digital fingerprints to the blocks :
To secure the blockchain and to check if the data has not been tampered , we use cryptographic hash functions . A hash table is an unordered collection of key-value pairs, where each key is unique. Hash tables offer a combination of efficient lookup, insert and delete operations. Hashing is the process of using an algorithm to map data of any size to a fixed length. This is called a hash value.
name=input("Enter your name")
hash1 = hash(name)
print("Hash(name) ={}".format(hash1))
The characteristics of an ideal hash function are:
- It should be easy to compute.
- It should be deterministic, meaning the same data will always result in the same hash.
- It should be uniformly random, meaning even a single bit change in the data should change the hash significantly.
The consequence of this is:
- It is virtually impossible to guess the input data given the hash. (The only way is to try all possible input combinations.)
- If you know both the input and the hash, you can simply pass the input through the hash function to verify the provided hash.
We generally use SHA-256 hash functions , but we will be using sha3_256
3. Chain the blocks
The blockchain is supposed to be a collection of blocks , we can store all the blocks in a tuple due to the immutability ,but that might not be enough .The solution is chaining of blocks , Every block has the hash value of it’s previous block.The point is what about the first block in the blockchain , well the first block is created by Owner of the block chain , know as the genesis block .
Now if someone tries to modify the content of a block , then the block ends up to new position in the blockchain , hence its previous block hash is changed , this can be observed by the nodes .
4.Proof of work algorithm
It is used to verify the ownership of block , as in which blockchain does it belong to, for example Blockchain A has blocks whose hash starts with 11 whereas Blockchain B has blocks whose hash starts with 00. We use nonce here,
A nonce is a number that we can keep on changing until we get a hash that satisfies our constraint. The nonce satisfying the constraint serves as proof that some computation has been performed. This technique is a simplified version of the Hashcash algorithm used in Bitcoin.
5.Add blocks to chain
To add a block to the chain, we’ll first have to verify that:
- The data has not been tampered with (the proof of work provided is correct).
- The order of transactions is preserved (the
previous_hashfield of the block to be added points to the hash of the latest block in our chain).
Mining :
Every transactions is originally stored as a pool of unconfirmed transactions , the process of confirming the authenticity of block and computing proof of work is know as mining of block ,
6.Create a platform to display all the information
We are using Python micro-frame\work called Flask , We will be up-scaling it Django ,which is also a Python framework
7.Establish consensus and decentralization
The main point of blockchain is decentralization , which means no single computer is the owner , there are nodes which are in-charge of the chain.
This decentralization part makes Blockchain unique .